Hosting a Custom .onion Hidden Service on Tor with Safety & Security Tips
This guide walks you through generating a vanity .onion address using mkp224o, configuring a Tor hidden service, serving content securely, and understanding the risk if your private key is leaked. It includes all commands for terminal execution, not embedded in any script.
1. Generate a Custom Vanity .onion Address
Install Dependencies
sudo apt update
sudo apt install -y build-essential autoconf automake libsodium-dev git
Clone the mkp224o Repository
git clone https://github.com/cathugger/mkp224o.git
cd mkp224o
Prepare the Build
chmod +x autogen.sh
./autogen.sh
./configure
make
Generate Vanity Onion Address
./mkp224o -d onions IMVICKYKUMAR # Replace with your preferred prefix
Check Generated Output
ls onions/
cat onions/IMVICKYKUMAR*/hostname
2. Install and Configure Tor
Install Tor
sudo apt update
sudo apt install tor -y
Enable and Start Tor
sudo systemctl enable tor
sudo systemctl start tor
Edit Tor Configuration
sudo nano /etc/tor/torrc
Add at the bottom:
HiddenServiceDir /var/lib/tor/hidden_service/
HiddenServicePort 80 127.0.0.1:8080
3. Replace Hidden Service Keys with Custom Onion
Stop Tor Before Replacing Keys
sudo systemctl stop tor
Replace the Default Hidden Service Directory
sudo rm -rf /var/lib/tor/hidden_service
sudo mkdir -p /var/lib/tor/hidden_service
sudo cp onions/IMVICKYKUMAR*/hs_ed25519* /var/lib/tor/hidden_service/
sudo chown -R debian-tor:debian-tor /var/lib/tor/hidden_service
sudo chmod 700 /var/lib/tor/hidden_service
Start Tor Again
sudo systemctl start tor
sudo systemctl status tor
4. Run Your Web Server on Port 8080
Example with Python
cd /var/www/html # Or directory of your site
python3 -m http.server 8080
Or Use Any App on 127.0.0.1:8080 (Flask, Node.js, etc)
5. Download and Install Tor Browser (Linux)
Download with wget
cd ~/Documents/TorService
wget https://www.torproject.org/dist/torbrowser/14.5.1/tor-browser-linux-x86_64-14.5.1.tar.xz
Extract and Launch
tar -xf tor-browser-linux-x86_64-14.5.1.tar.xz
cd tor-browser_en-US
chmod +x start-tor-browser.desktop
./start-tor-browser.desktop
6. Security Risk: If Your Private Key is Exposed
If your hs_ed25519_secret_key is exposed (e.g., uploaded to GitHub):
-
A hacker can host their own service on your
.onionURL -
They can serve malicious content impersonating you
-
Visitors would be unaware as the
.onionaddress remains unchanged
How?
Tor calculates the .onion URL from the public key → from private key. If an attacker has the private key, they can generate the same URL and bind it to their own port 8080, serving their content instead of yours.
7. Prevent Leaks with .gitignore
Add to .gitignore
onions/
*.key
hs_ed25519_secret_key
This ensures your private keys are not accidentally committed to version control.
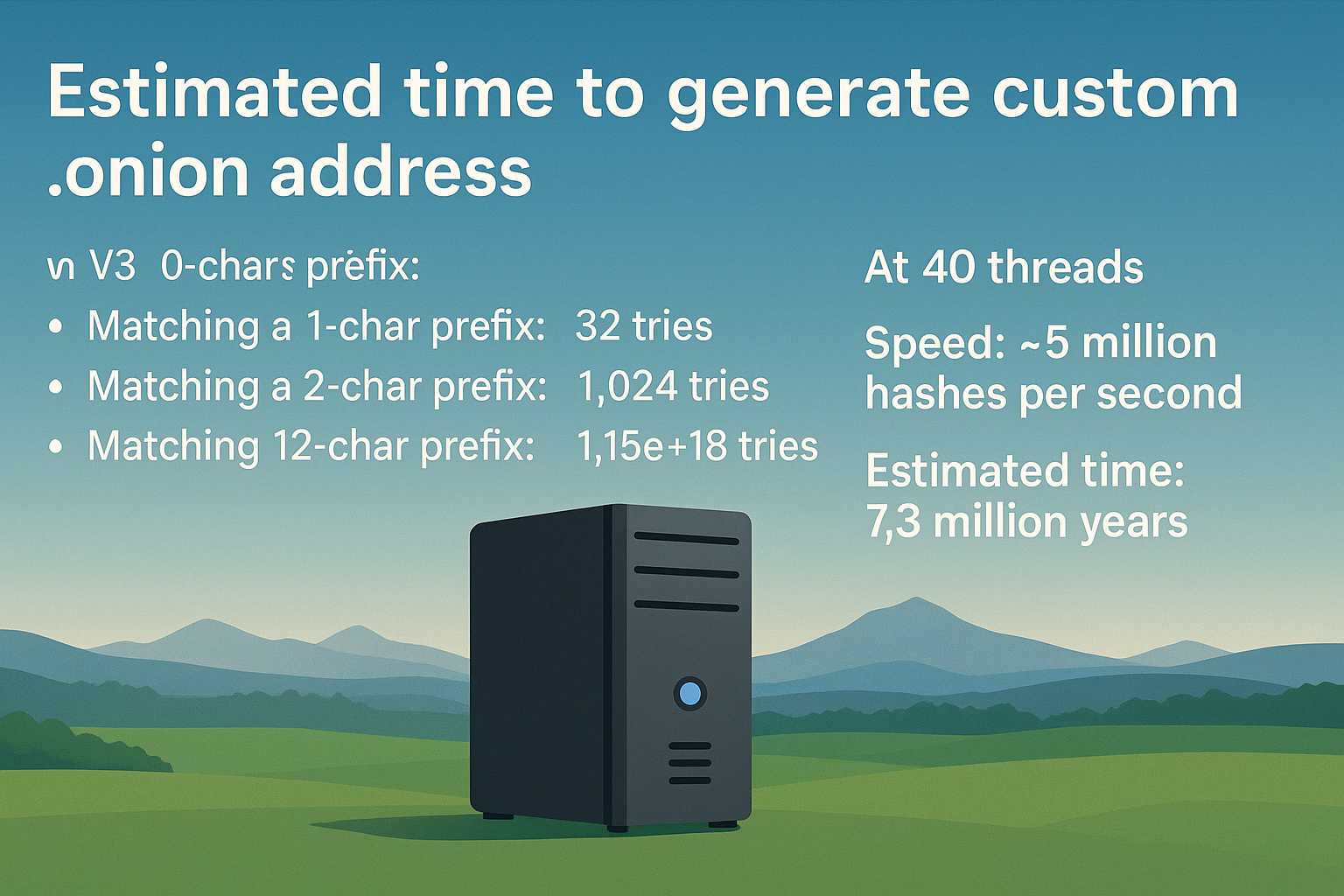
Vanity Generation Speed Estimates
| Machine Type | Threads | Prefix | Est. Time |
|---|---|---|---|
| Laptop (i7-6500U) | 4 | 6-char | 10–20 mins |
| 7-char | 6–12 hours | ||
| Desktop (i7-9700K) | 8 | 7-char | 3–6 hours |
| Server (Xeon 6138, 40 CPU) | 40 | 8-char | 1–2 hours |
| Cloud (32 vCPU AVX2) | 32 | 8-char | 30–60 minutes |
Time increases exponentially per character — 1 extra char = ~32× more time.
Conclusion
-
Keep your private key secret and secure
-
Do not upload key files to GitHub or any remote system
-
Regularly audit your repositories and
.gitignorerules
By following this guide, you can confidently run a Tor hidden service with a custom vanity URL and safeguard it from impersonation.







1 Comments
Vicky Kumar
Created my custom onion URL starts with "imvicky", because "imvickykumar" will take millions of years. 😭🤣 https://x.com/imvickykumar999/status/1923794478797631524